They think of viruses that infect an organization from the outside.They envision hackers breaking into their information vaults.
 们考虑来自外部的感染公司的病毒,
们考虑来自外部的感染公司的病毒, 们设想黑客侵入到信息宝库中。
们设想黑客侵入到信息宝库中。
 机迷
机迷
 脑资料者;
脑资料者;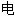 脑“黑客”
脑“黑客” 机黑客
机黑客They think of viruses that infect an organization from the outside.They envision hackers breaking into their information vaults.
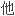 们考虑来自外部的感染公司的病毒,
们考虑来自外部的感染公司的病毒,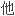 们设想黑客侵入到信息宝库中。
们设想黑客侵入到信息宝库中。
After these hackers are atttacking a website normally, replace website content into the page that contains remonstrant content, affix anarchism mark, still leave their assumed name.
这些黑客通常会在攻击网站后,把网站内容替换成带有抗议内容的页面,并贴上无政府主义标志,还
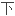
 们的化名。
们的化名。
Finding good code to read used to be hard, because there were few large programs available in source for fledgeling hackers to read and tinker with.
过去找到适合阅读的好的代码是困难的,因为几乎没有大型程序的源代码能让新手练手。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。